It has been observed that nearly 60% of organizations are a victim of email compromise attacks. And over the past few years, cybersecurity practitioners have faced an immense challenge to keep up with the latest technique by gaining initial access to your environment by deploying malware.
With this, Microsoft has expanded its cybersecurity suites, such as Microsoft 365 Defender, which uses AI-based capabilities to auto-detect and disrupt cyberattacks like business email compromise (BEC) and ransomware attacks. Both these scams can be very costly to the victims, therefore, needs a high level of protection. To prevent the BEC attacks, Microsoft defender for office 365 detects attacks and removes access from the environment. It helps to switch from the compromised account and limits their ability to send any fake emails or prevent them from transferring money to the fraudulent account. In this post, let’s understand what BEC is, how BEC works, and how to avoid it.
What is BEC (Business Email Compromise)?
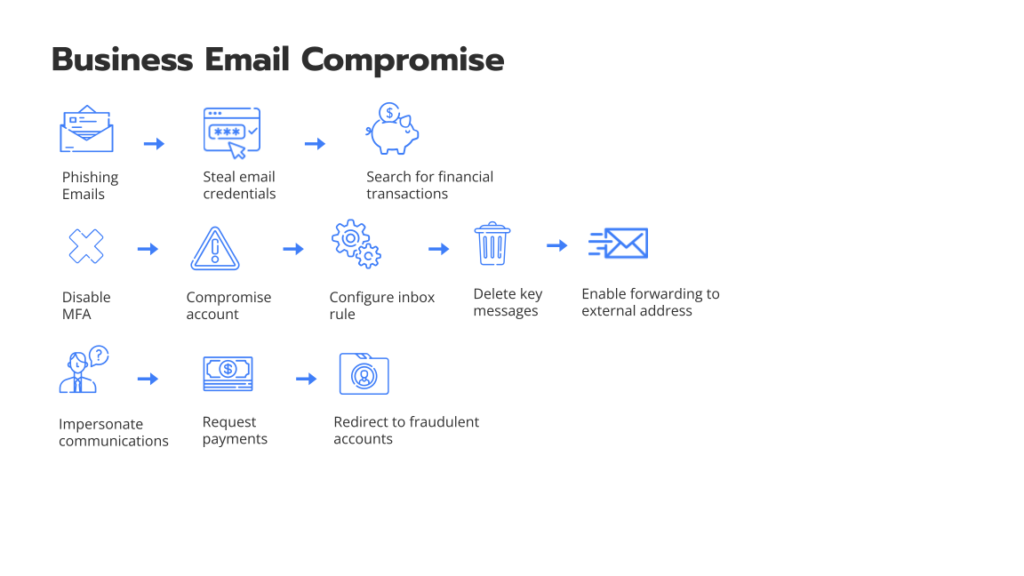
Business Email Compromise (BEC) is one type of cybercrime that provide access to users’ email and trick them into sending money or else they’ll spread the company’s confidential information. Here, the culprit will pose as a trusted figure and then ask for a fake bill to use in another scam. With this, BEC is growing rapidly and has increased after the rise of remote work. In short, BEC is one dangerous and expensive kind of phishing attack, which can cost businesses billions of dollars lost each year.
What are the different types of BEC (Business Email Compromise) scams?
CEO Fraud
In this scam, the attackers will be putting themselves as CEO or an executive of the company. They will send an email to the company’s employees and financial department requesting to transfer the money into their account.
Account Compromise
The user’s email account is hacked and is used to request payment from vendors. Later the payments are sent to various fraudulent bank accounts, which are owned by attackers.
False Invoice Scheme
The attackers in this scam will target foreign suppliers. Here, the attackers act as suppliers and request another party to send funds to their fake accounts.
Attorney Impersonation
In this scam, the attacker will impersonate the lawyers or any low-key representatives to target using various attacks commonly. Also, they don’t have much knowledge about the validity request.
Data Theft
It’s an attack that only targets HR employees in an attempt to get a piece of information about the sensitive data of any individuals within the company. Later the information is used for the future and can be used as CEO Fraud.
Business Email Compromises (BEC) Prevention with Microsoft 365 Defender
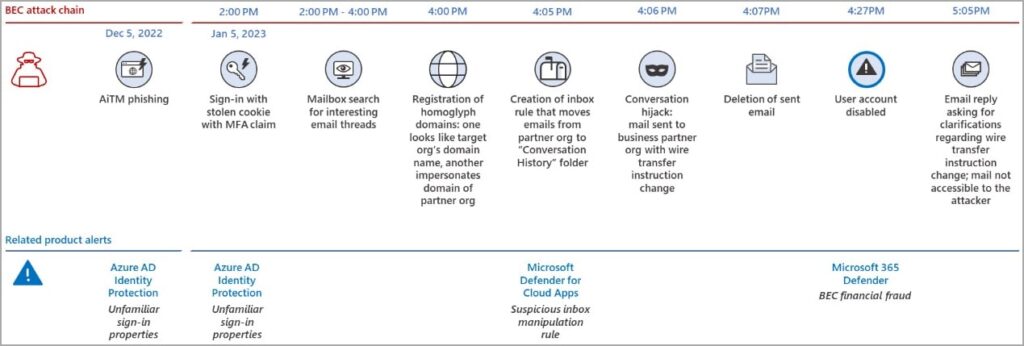
Business Email Compromise attacks are a multi-billion problem that targets your organizations through phishing, social engineering, or can buy account credentials from the dark web. In one of the Twitter threads, Microsoft analyzed that the BEC scam began with a threat actor who performed an adversary in the middle (AiTM) phishing attack by stealing the target session cookie and bypassing it through MFA protection.
The thread says the attacker logged into the victim system on 5th January 2023 and spent two hours looking in the mailbox for good email threads to hijack. Talking about thread hijacking is a technique in which the message continues an existing communication exchange, allowing the recipient to trust them. Later the attackers register it through a deceptive domain and make it look identical to the sites of their targeted organization.
With this, the attacker will create an inbox email to the partner organization in their specific folder.
Later in the next 5-10 minutes, they will send a wire transfer mail along with transfer details. The victim must delete it immediately to reduce the likelihood of the compromised breach. At this point, Microsoft defender comes in. Microsoft 365 Defender has game-changing capabilities and limits a threat by reducing the overall attack impact associated with the loss of productivity.
Microsoft 365 defender generates a BEC warning 20 minutes after the attack is made. The mail is deleted and sent to an automatically disrupted folder by disabling the user’s account of attackers.
You can connect with a Microsoft defender consulting services provider company and understand how Microsoft defender for office 365 works. When it does test, BEC detects the actions in the customer’s environment which are faced by real-world scenarios. Using Microsoft defender, one can prevent dozens of emails and disable them automatically. Also, it’s claimed by Microsoft that it offers security products that are disrupted by 38 BEC attacks and target organizations by using the confidence eXtended detection and Response signals across all emails, identities, endpoints, and SaaS applications.
Wrapping Up
Lastly, Microsoft comes with new highlighted and automatic actions that can be easily tailored. Moreover, connecting with Microsoft Defender consultants can guide you properly in understanding how one can prevent Business Email Compromise attacks.
In addition to this, choose an organization that comes with experience and reputational methods. They should help in damage control and gain the customer’s trust as the experts have the ability to assist you in combining technical and non-technical controls along with guarding them in protecting against these attacks. Connect with the best Microsoft Defender consultant service company and help your customers mitigate BEC and verify the attacks through various sources.

